Businesses today encompass multiple devices, multiple points of entry and multiple employees. Stopping advanced threats from reaching your devices, data and users requires a layered defense.
Our IT Security Suite provides your business with solid protection against phishing threats and social engineering, through integrated cloud-based services that analyze traffic across all of the major threat vectors.
Email Security Monitoring
Advanced threat protection for incoming mail, email encryption for outgoing while preventing sensitive email data from leaving your organization.
One example of how Email Security Monitoring protects your business: In your organization, email security monitoring could stop an employee email because it contains a social security number or other sensitive information that shouldn’t be emailed.
Risk Scanning
Continuous vulnerability scanning and endpoint analytics managed by security experts helps your organization make sense of risk to reduce your risk of attack.
One example of how Risk Scanning protects your business: Vulnerability scanning will scan for security holes in your systems. This might look like your internet browser having a vulnerability that opens you up to internet threats as you innocently browse the internet.
Sentinel
By detecting out-of-the-ordinary communication patterns, this real-time protection prevents business email compromise and account takeover.
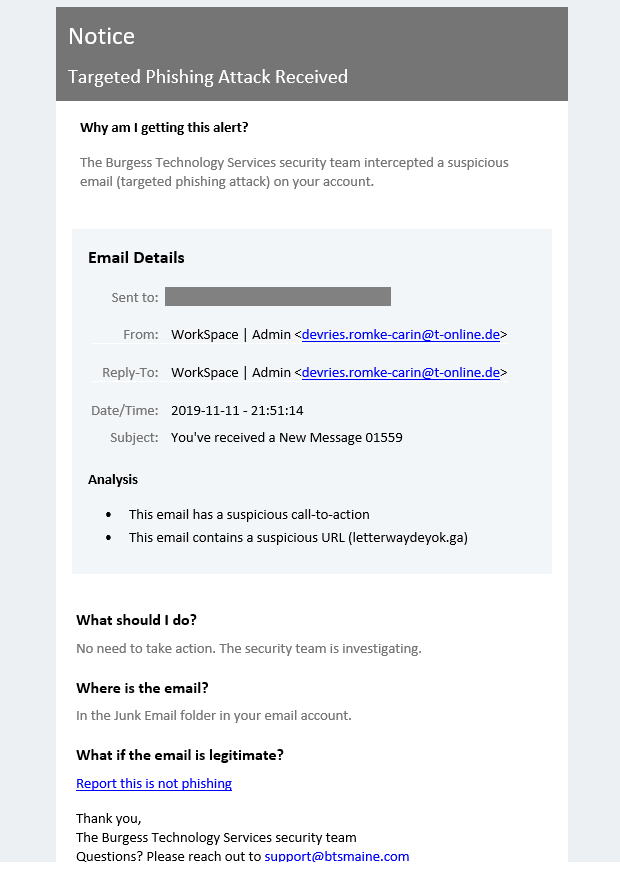
One example of how Sentinel protects your business: automatic interception of suspicious emails before they reach your inbox or that of your employees. Emails are sent to alert the user that a Phishing Attempt has been detected and provides additional information on steps to take. (see example at the end of this blog post)
Security Awareness Training
Today, employees are frequently exposed to sophisticated phishing and ransomware attacks. Our security awareness training and simulated phishing platform helps you manage the risk of social engineering.
One example of how Security Awareness Training protects your business: We use simulated phishing attacks, sent to your employees, to test whether or not they will fall for them. The results dynamically train employees by instantly showing them the hidden red flags they missed within that email.
Two-Factor Authentication
Two-factor authentication adds an additional layer of security to the login process by making it harder for attackers to gain access to a person’s devices, online accounts and business networks.
One example of how Two-Factor Authentication protects your business: Working remotely or accesses the business network from outside the office? Two-factor authentication would require a code sent to your cellphone that needs to be entered into your laptop login process.
Sentinel Example
Reader Interactions