Phishing Emails to Watch Out For
We’ve seen a lot of recent email phishing attempts that we’d like you to be aware of. Phishing emails try to convince you to open links that could be harmful to your computer and/or network and your personal identity.
- Remember to always think before you click.
- Never click on any links or open any attachments in unsolicited emails.
- Delete suspicious emails right away and be sure to remove them from your trash folder.
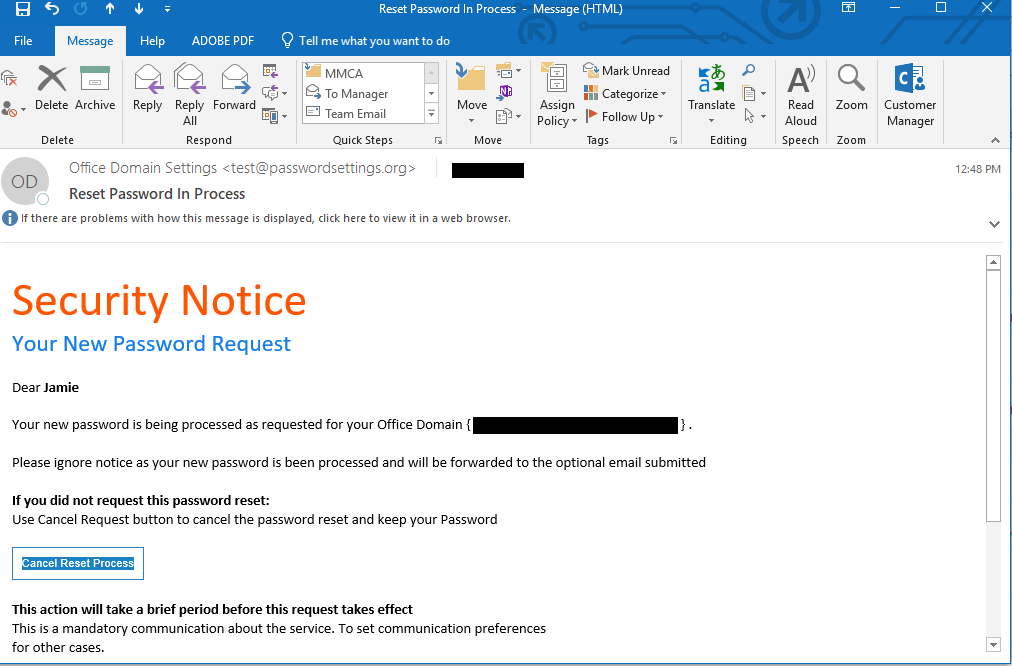
Phishing Attempt #1
This phishing attempt is disguised as an email from Microsoft. It wants the recipient to think someone reset their password and to cause panic. Ultimately, they are trying to get the user to click the BOGUS cancel request.
DO NOT CLICK ANY LINK!
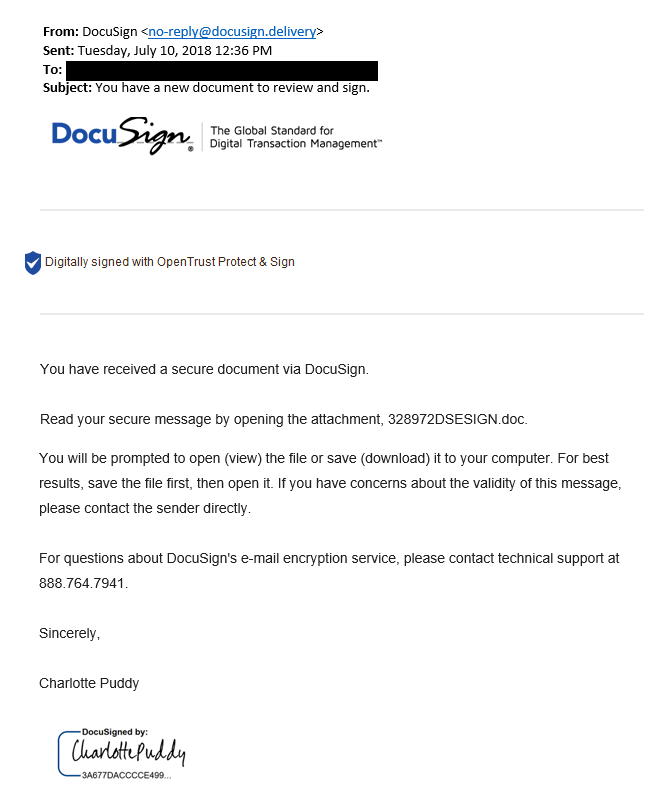
Phishing Attempt #2
This phishing attempt tried to get the user to open a malicious attachment by piquing the interest of the recipient and appearing legitimate, even though it is not.
NEVER open unsolicited attachments.
Attempt #3 Blackmail Phishing
Blackmail phishing emails attempt to scare you into paying a high priced ransom to “protect your reputation”. It’s possible that the email may even contain a password you have used in the past, or are currently using.
Don’t panic. Just be sure that the password listed in the email is not a valid one. If it is, change it. Then do a full system scan, or call us and we’ll be happy to help (207) 443-9554.
Do NOT pay the ransom. DO NOT REPLY, and DO NOT CLICK LINKS that may be in the message.
Delete the message and be sure to remove it from your Trash folder.
How did they get your old password?
A number of people have said that they received a version of the email which includes a real password they’ve used in the past. Does this mean that they should be concerned? The answer is No and Yes.
No, you shouldn’t be concerned that your computer was hacked – it’s still a scam.
But, yes, you should be concerned that your password has been leaked through a data breach. Security researchers have uncovered more than 500 million passwords leaked through these breaches. That password in the email was likely one of them.
Blackmail Phishing Attempt Example
Dear XYZ,
I’m aware, Soccer123, is your pass word. You may not know me and you’re probably wondering why you are getting this e-mail, correct?
actually, I placed a malware on the adult videos (porno) web-site and you know what, you visited this website to experience fun (you know what I mean). While you were watching videos, your internet browser started operating as a RDP (Remote Desktop) with a keylogger which provided me accessibility to your screen and web cam. Just after that, my software program gathered every one of your contacts from your Messenger, FB, and email.
What did I do?
I made a double-screen video. 1st part shows the video you were viewing (you have a good taste hahah), and second part shows the recording of your cam.
What should you do?
Well, in my opinion, $2900 is a reasonable price for our little secret. You will make the payment via Bitcoin (if you don’t know this, search “how to buy bitcoin” in Google).
BTC Address: xxxxNEsAyxMKzHnNKjkoyxxxxx
(It is cAsE sensitive, so copy and paste it)
Important:
You have one day in order to make the payment. (I have a unique pixel within this e-mail, and at this moment I know that you have read this email). If I don’t get the BitCoins, I will definately send your video to all of your contacts including friends and family, coworkers, and many others. However, if I do get paid, I will erase the video immidiately. If you need evidence, reply with “Yes!” and I will send your video recording to your 14 friends. It’s a non-negotiable offer, that being said please do not waste my time and yours by replying to this email.
——
Security Awareness Training
How confident are you that your employees would know what to do in this situation?
People are used to having a technology solution, but social engineering bypasses all technologies, including firewalls. Technology is critical, but we have to look at people and processes. Social engineering is a form of hacking that uses influence tactics.
Reader Interactions