In the IT Support sphere, we always need to be aware of current and evolving threats to your business network, so it’s always a good time to be taking a look at the most recent iterations of spam, scams, phishing and hacking attempts. Here’s what we’re seeing a lot of lately:
Trusted Vendor Pop-ups
You’re sitting at your computer and a window pops up, branded as a Microsoft and Windows alert. It’s alarming. It tells you several times the numerous ways you are at risk. It may give you a time limit for contacting them to save the day. It repeats the phone number you must call to do so. When you call them, they ask for access to your computer (of course, legit IT support would do the same, as you have previously experienced no doubt.) They then attack you in a few potential ways: Access your contacts, so they can attack others; access your passwords, the keys to the kingdom, including your bank log-ins which can lead to tens of thousands of dollars lost. They might poke around in your computer and bring up a DOS screen which looks like gibberish to you, as proof of your infection. They may ask you to pay a fee for their assistance in cleaning $299, $499, whatever. And on and on it can go.
Savvy, intelligent people fall for this every day. Because the bad guys know the trigger words to both alarm us about the threat, and make us trust them to assist.
Here’s what to do if you get this pop-up. Shut your computer down. Don’t click any links or buttons related to the pop-up, (not even an X to close) and don’t call any numbers. Hold your power button in for 10 seconds until it powers down, and then call your *local* IT company. It probably makes sense to have your machine looked over. The fee for a quick cleanup/assessment is much, much lower than a financial and security loss to the bad guys.
Trusted Vendor Phishing Emails
We’re seeing a lot more of this lately.
Emails from Norton thanking you for your $500 payment and you don’t even have Norton. You panic thinking they may have somehow gotten your money. They ask, “Did you authorize this? No problem, click this link or call this number for assistance.” Of course, they’ll need your banking information so they can back out the payment. No. Just no. Don’t call. Don’t click. Watch your bank account and you will see, no payment will come out. Keep it that way!
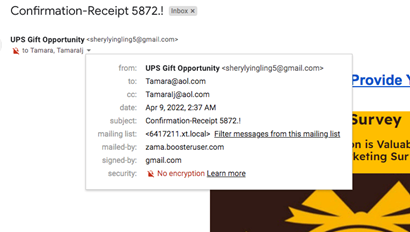
Emails from UPS about a prize you could win by filling out a brief survey. These are getting much shinier. UPS brand colors and logo. Enticing color graphics. But don’t be fooled, take a look at the details in the to: and from: and you’ll immediately see the problem. Also – remember that hovering over links may well show you that they do not go where they purport to. Don’t click. Just delete the email and move on.

Tempting Texts
We’re also seeing short and sweet texts coming in thanking us for our Verizon payment, alerting us to an arriving FedEx or UPS package, or again offering us prizes for a short survey. Again, if you are not expecting such things, or even if you are, don’t click. One of our staff recently received the Verizon thank you around the time her monthly payment was posted, but she’d never signed up for these texts. You can go to the vendor websites to check on payments and deliveries, but don’t be tempted to click on anything you are not sure of. Scammers bank on the law of percentages. Like sending you messages about your car warranty and school loans that you don’t even have. They will successfully hit people who do have a student loan, or who do use Verizon, and may be easily fooled. If you question a messages legitimacy, do a quick google search on the topic, phrasing or phone number, and chances are you’ll find lots of reports on how it’s a scam. It’s just never worth the risk, so train yourself to not click on unexpected links at any time.
BEC: Hacking and Spoofing
We recently shared an FBI alert regarding BEC (Business Email Compromise) attacks, which is a very good read with regard to this topic. (Read original alert here.) Our support staff has seen an uptick in Hacking Attempts and Spoofed Emails the past year as criminals become more savvy, especially with social engineering and focused attacks. Here is an excerpt from the FBI piece.
Scammers might:
- Spoof an email account or website. Slight variations on legitimate addresses (john.kelly@examplecompany.com vs. john.kelley@examplecompany.com) fool victims into thinking fake accounts are authentic.
- Send spearphishing emails. These messages look like they’re from a trusted sender to trick victims into revealing confidential information. That information lets criminals access company accounts, calendars, and data that gives them the details they need to carry out the BEC schemes.
- Use malware. Malicious software can infiltrate company networks and gain access to legitimate email threads about billing and invoices. That information is used to time requests or send messages so accountants or financial officers don’t question payment requests. Malware also lets criminals gain undetected access to a victim’s data, including passwords and financial account information.
How to Protect Yourself
- Be careful with what information you share online or on social media. By openly sharing things like pet names, schools you attended, links to family members, and your birthday, you can give a scammer all the information they need to guess your password or answer your security questions.
- Don’t click on anything in an unsolicited email or text message asking you to update or verify account information. Look up the company’s phone number on your own (don’t use the one a potential scammer is providing), and call the company to ask if the request is legitimate.
- Carefully examine the email address, URL, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.
- Be careful what you download. Never open an email attachment from someone you don’t know, and be wary of email attachments forwarded to you.
- Set up two-factor (or multi-factor) authentication on any account that allows it, and never disable it.
- Verify payment and purchase requests in person if possible or by calling the person to make sure it is legitimate. You should verify any change in account number or payment procedures with the person making the request.
- Be especially wary if the requestor is pressing you to act quickly.
When you are running a business, it’s difficult to keep up with all the potential threats and keep your employees (and in turn your network) safe. We highly recommend Security Awareness Training to beef up your first line of defense (your staff) and Network Monitoring to stop the threats in their tracks if they get access. Email info@BTSMaine.com for more details.
We’ve covered security, scams, phishing and other threats in several previous blogs and podcasts. Check some of them out here: (in the blog these will have just pertinent titles that link to these urls)
https://itsuckspodcast.com/it-security-suite-by-bts
https://itsuckspodcast.com/dr-frank-appunn-on-cybersecurity
https://itsuckspodcast.com/security-awareness-training
https://itsuckspodcast.com/email-attacks-scams-and-phishing
https://www.burgesstechnologyservices.com/burgess-technology-blog/it-security-suite/
Reader Interactions